Hardware / Firmware
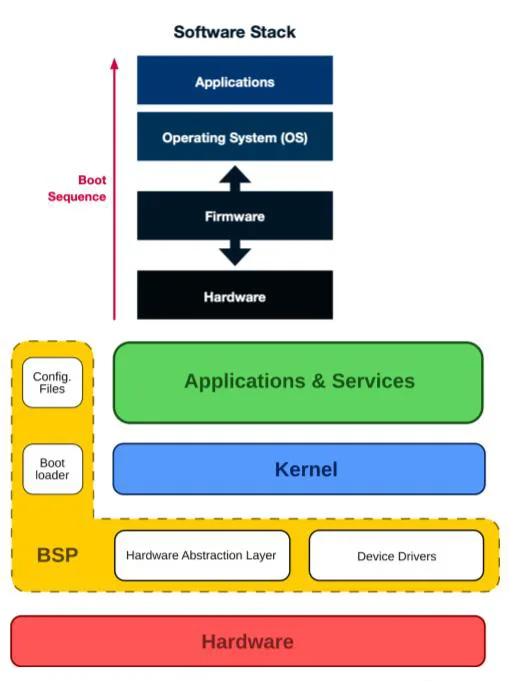
- Risks: Physical tampering, side-channel attacks, bootkits.
- Controls: Secure boot, hardware root of trust, firmware signing, measured boot, and Information Flow Tracking
Note: Hardware compromise undermines higher layers → trust must start here.

