Information Flow Tracking
- Information Flow Tracking(IFT):
- The core concept of the IFT technique is to represent the information/data flow propagation across the system by labeling the data objects with a security class and tracking the label during data calculation.
- It verifies or controls data movement by implementing security flow regulations,
- where an information Flow Model (FM) is established,
- Describing the permissible flow of information among N data objects using the security class SC and flow relation.
- An informative flow model FM, is specified for the DUT
1. M. K. Munigala, S. Sood, M. K.N and K. Baladaniya, “A Novel Security Vulnerability Detection Mechanism Using Information Flow Tracking on a Complex SOC,” 2022 IEEE Asia-Pacific Conference on Computer Science and Data Engineering (CSDE), Gold Coast, Australia, 2022, pp. 1-6, doi: 10.1109/CSDE56538.2022.10089277.
Example
- We have a system with 2 data objects A and B
- Goal: Check for security vulnerability when computing value C from A and B
- Define the tags, describing the security classes of A, B, and C, respectively.
- Using the IFT, check if the data from A and B is “allowed” to update security class C, i.e. do the security access rules permit this
IFT Definition of SOC NCA
- For a given register in SOC, figure out all the NCPs.
- Generate NCA from NCP
- The security of any register is equal to access control security
- NCA is secure if and only if all its NCP’s are in trust boundary to access a specific register.
IFT for SOC
1. Storage objects = SOC registers
2. NCP is a path for data to reach those storage objects
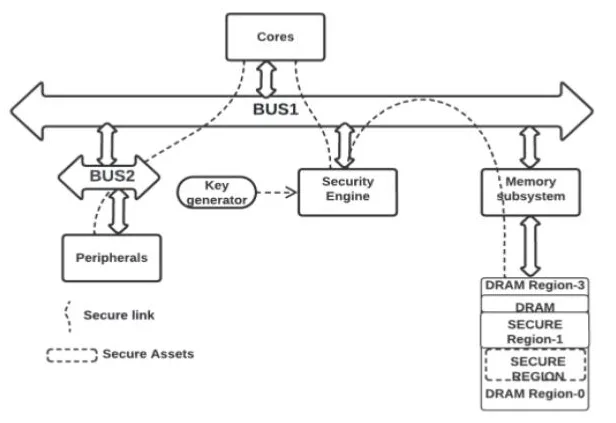
Evidence
Approach is applied on one of the Intel’s SOC