The Growing Need for Secure FPGA Development
According to Swirski and Beetlebox, (2024), Field Programmable Gate Arrays (FPGAs) are at the forefront of modern hardware innovation, providing unparalleled flexibility and performance. However, this adaptability comes with inherent security risks that can expose hardware and software components to malicious attacks. Security threats such as substitution attacks, side-channel attacks, and FPGA Hammer exploit vulnerabilities in FPGA systems, making them prime targets for adversaries. Organizations must adopt proactive security measures throughout the FPGA development lifecycle to mitigate these risks.
Integrating Security with DevSecOps
DevSecOps extends the principles of DevOps by embedding security at every stage of the development pipeline, as highlighted by Swirski and Beetlebox, (2024). Instead of treating security as an afterthought, DevSecOps ensures that security is integrated from the initial design phase to deployment and monitoring. FPGA development teams can significantly reduce vulnerabilities and strengthen system resilience against cyber threats by implementing continuous security testing, automated compliance checks, and real-time threat detection.
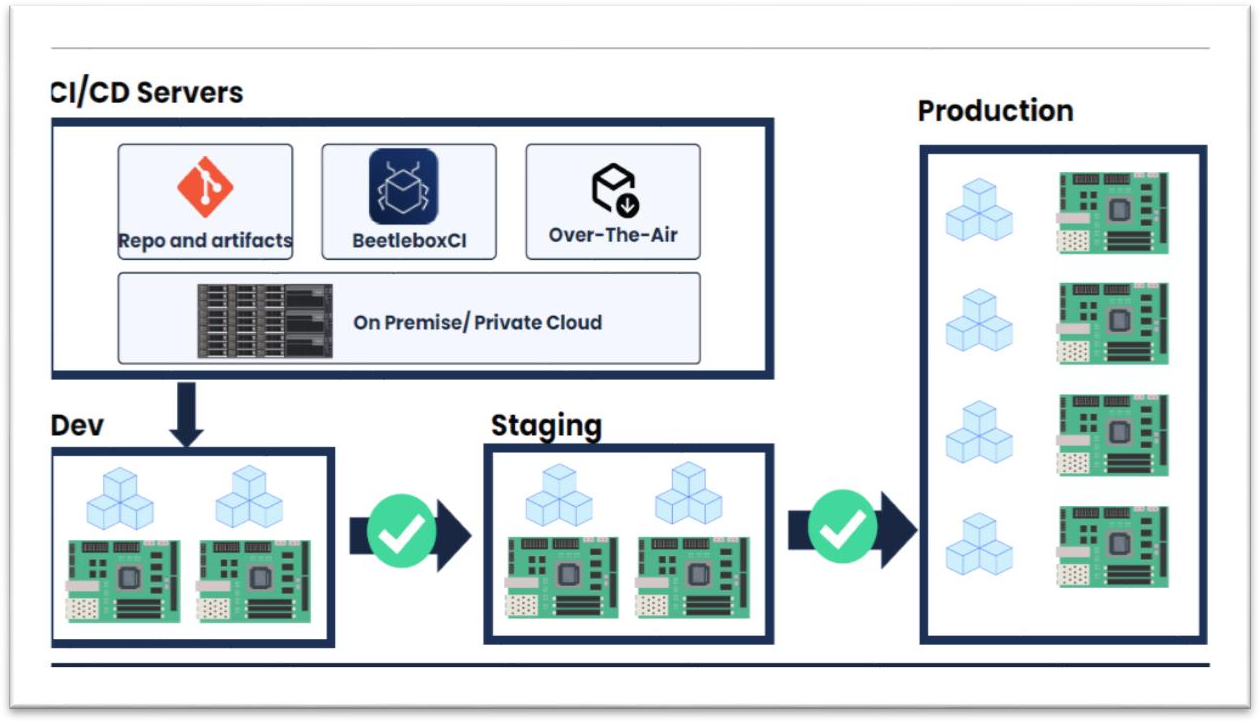
The figure below illustrates how the system enforces security throughout the development, staging, and production phases in the physical architecture of a secure FPGA CI/CD pipeline. By leveraging on-premise or private cloud CI/CD servers, including repository management, BeetleboxCI, and over-the-air updates, organizations can streamline FPGA development while ensuring robust security practices.
Figure 1: Physical Architecture
Key Components of a Secure FPGA DevSecOps Pipeline
A well-structured FPGA DevSecOps pipeline incorporates several best practices to safeguard against security risks, as mentioned by Swirski and Beetlebox, (2024). Threat modeling identifies potential attack vectors early, while Static Application Security Testing (SAST) detects code vulnerabilities before developers commit them. Secure boot image encryption protects FPGA configurations from tampering, while continuous monitoring systems track behavior to identify any anomalies in real-time. These components collectively form a robust security framework for FPGA development.
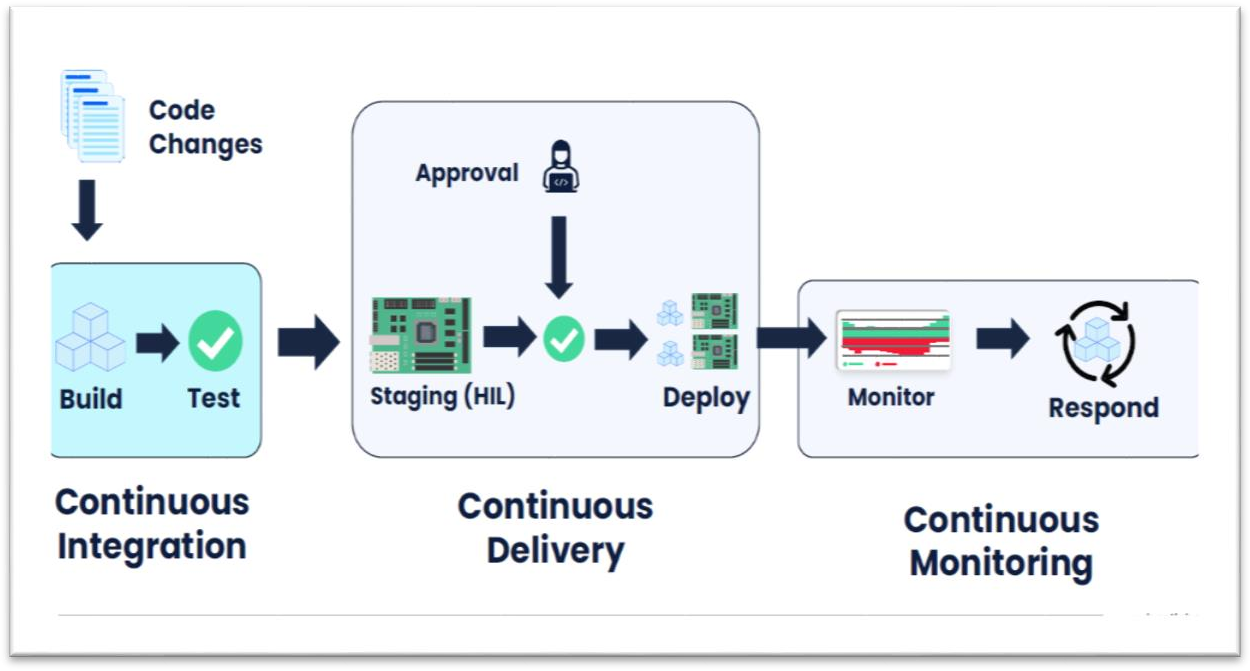
The Continuous Delivery Pipeline embeds security from code changes to monitoring at every stage. As depicted in the image below, FPGA development follows a structured approach that includes continuous integration, hardware-in-the-loop (HIL) staging, and deployment, with real-time monitoring and response mechanisms to detect and mitigate threats effectively.
Figure 2: Continuous Delivery Pipeline
Implementing DevSecOps for FPGA Development
Successfully integrating DevSecOps into FPGA pipelines requires a systematic approach, as noted by Swirski and Beetlebox, (2024). The process begins with detailed threat modeling and agile security planning, followed by secure coding practices that include automated vulnerability scans. We apply security checks to the bitstream generation and synthesis processes during the build phase. Rigorous testing methodologies, including simulation, emulation, and hardware-in-the-loop testing, validate the security posture of the FPGA system. Finally, secure deployment practices ensure continuous protection, including encrypted over-the-air (OTA) updates and real-time monitoring.
The Future of Secure FPGA Development
In an era where cyber threats are growing more sophisticated, securing FPGA pipelines with DevSecOps is no longer optional—it is essential, as emphasized by Swirski and Beetlebox, (2024). Organizations that integrate security into their development workflows can safeguard their FPGA systems from evolving threats while ensuring compliance with industry standards. Companies like Beetlebox are in charge of FPGA security, offering expertise and resources to help businesses implement DevSecOps successfully. By embracing this proactive approach, organizations can build resilient, future-proof FPGA solutions that stand the test of time.
Note: For those interested in the latest advancements in verification technologies, the FPGA Verification Event 2025 (Verification Futures UK) offers an excellent opportunity to gain insights into cutting-edge verification practices.
References
Swirski, A. & Beetlebox. (2024). Securing FPGA Development Pipelines with DevSecOps. https://www.beetlebox.org

Written by : Mike Bartley
Mike started in software testing in 1988 after completing a PhD in Math, moving to semiconductor Design Verification (DV) in 1994, verifying designs (on Silicon and FPGA) going into commercial and safety-related sectors such as mobile phones, automotive, comms, cloud/data servers, and Artificial Intelligence. Mike built and managed state-of-the-art DV teams inside several companies, specialising in CPU verification.
Mike founded and grew a DV services company to 450+ engineers globally, successfully delivering services and solutions to over 50+ clients.
Mike started Alpinum in April 2025 to deliver a range of start-of-the art industry solutions:
Alpinum AI provides tools and automations using Artificial Intelligence to help companies reduce development costs (by up to 90%!) Alpinum Services provides RTL to GDS VLSI services from nearshore and offshore centres in Vietnam, India, Egypt, Eastern Europe, Mexico and Costa Rica. Alpinum Consulting also provides strategic board level consultancy services, helping companies to grow. Alpinum training department provides self-paced, fully online training in System Verilog, UVM Introduction and Advanced, Formal Verification, DV methodologies for SV, UVM, VHDL and OSVVM and CPU/RISC-V. Alpinum Events organises a number of free-to-attend industry events
You can contact Mike (mike@alpinumconsulting.com or +44 7796 307958) or book a meeting with Mike using Calendly (https://calendly.com/mike-alpinumconsulting).
Stay Informed and Stay Ahead
Latest Articles, Guides and News
Explore related insights from Alpinum that dive deeper into design verification challenges, practical solutions, and expert perspectives from across the global engineering landscape.