Introduction
For semiconductor and embedded software stakeholders, clarity around compliance, certification, and verification is critical. Engineers, tool vendors and decision-makers rely on these concepts to ensure processor designs are robust, interoperable and trusted across ecosystems. Misunderstandings can result in design flaws, costly re-spins, or delays in bringing products to market. By distinguishing these terms and examining industry methodologies, we can see how leading organisations such as ARM, RISC-V International, PCI-SIG and USB-IF approach the problem of ensuring consistency and quality.
Definitions: Compliance, Certification and Verification
Verification is the internal engineering process of checking that a design behaves as intended. It involves simulation, formal analysis, and test execution to confirm that a product conforms to its specifications and is free of functional errors.
Compliance is the process of ensuring a design or product meets the requirements of an external specification or standard. A system-on-chip (SoC) can only claim compliance if it behaves according to the relevant ISA or protocol (for example, an SoC implementing the USB standard correctly).
Certification is formal recognition by an independent body that a design or product meets compliance criteria. Certification programmes typically allow logos (for example, “USB Certified”) and provide end-users with trusted assurance.
Relationship Between Verification, Compliance and Certification
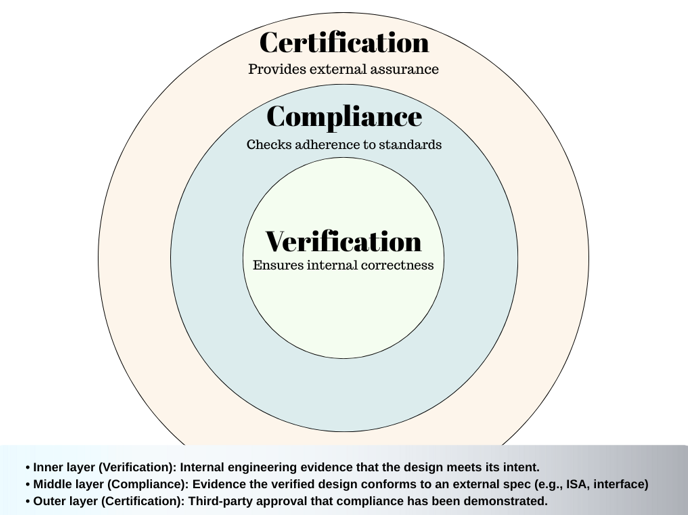
Verification, compliance, and certification are not isolated steps but interconnected processes that ensure quality and trust in semiconductor and software systems. Verification establishes internal confidence by proving that a design behaves as intended. Compliance extends this by checking that the design adheres to formal specifications or standards, ensuring product interoperability. Certification adds a final, external layer of assurance, providing an independent stamp of approval that the product meets defined industry requirements.
These three dimensions overlap: verification forms the foundation, compliance builds on it with specification-driven tests, and certification envelops both with formal recognition. The diagram below illustrates this layered relationship.
Figure 1: Relationship between Verification, Compliance, and Certification
ARM’s Approach and Importance to Customers
ARM’s business depends on multiple licensees implementing its architectures. ARM emphasises rigorous verification and compliance testing over external certification to preserve consistency. Its CPU designs undergo extensive verification cycles (reportedly 10^15 per core design) to ensure correctness.
Unlike open standards, ARM itself validates compliance. Companies must pass ARM’s Architectural Validation Suite (AVS) to be approved as ARM-compliant for custom cores built under an ARM architecture licence. In other domains, ARM does operate certification schemes, such as SystemReady, which validates that hardware platforms are interoperable with operating systems.
For customers, this methodology provides three advantages:
- Software developers can rely on consistent execution of the instruction set, ensuring applications run across multiple ARM-based platforms.
- Device manufacturers benefit from trusted interoperability, reducing integration issues and accelerating time-to-market.
- SoC vendors can leverage “known good IP”, cutting verification costs and risks.
This strong compliance and verification culture underpins ARM’s reputation for reliability and explains why its IP is trusted across global markets.
ARM’s Compliance Support for Partners
ARM supports licensees and ecosystem partners with multiple layers of compliance and verification assistance:
- Documentation and specifications provide exhaustive architectural reference manuals.
- Architectural Validation Suite (AVS) ensures custom cores are tested against the ISA.
- Fast Models act as golden simulation references.
- SystemReady ACS checks platform-level compliance for interoperability.
- Functional safety packages (such as the Cortex-R5 Safety Package) help licensees demonstrate compliance with standards such as ISO 26262.
- Ecosystem consultation offers training, guidance and verification IP to partners.
These mechanisms enable ARM’s partners to deliver consistent, compliant products across markets ranging from mobile handsets to automotive systems.
Compliance in Industry Standards: PCIe and USB
In contrast to ARM’s proprietary model, industry consortia such as PCI-SIG and USB-IF operate open compliance and certification frameworks.
| Standard | Governing Body | Compliance Process | Certification Output | Market Impact |
| PCIe | PCI-SIG | Electrical and protocol compliance tests plus interoperability workshops | Listing on PCI-SIG Integrators List | Guarantees interoperability across add-in cards, motherboards and systems |
| USB | USB-IF | Compliance workshops and certified third-party labs using official tools | Use of USB logos and public certification | Builds consumer trust and cross-vendor device compatibility |
Table 1: PCIe vs USB Compliance Programmes
These approaches show compliance and certification working together: compliance tests validate adherence to the standard, and certification programmes give the market visible assurance. ARM’s approach, by contrast, is proprietary, with compliance managed internally and certification used selectively.
Alternative Approaches: Intel x86 and SPARC
Intel’s x86 architecture represents a closed verification model. Intel and AMD implement the ISA under cross-licensing agreements, with verification suites kept proprietary. Compliance is enforced internally rather than through public workshops or certification programmes. This ensures consistency but lacks transparency.
SPARC International, by contrast, provided a consortium-driven compliance model. Multiple vendors could implement the ISA, but only after passing official compliance tests maintained by the consortium. This structure, similar to PCIe or USB, ensured interoperability and prevented fragmentation.
ARM historically mirrored Intel’s approach, controlling the ISA centrally, whereas RISC-V is now adopting a more SPARC-like, open compliance model.
Compliance Methodology Approaches
Compliance methodologies vary significantly between proprietary and open ecosystems, and ARM and RISC-V represent two contrasting models. ARM enforces compliance through a tightly controlled, top-down approach, using proprietary validation suites, reference models, and staged approval processes. This approach guarantees consistency across licensed implementations but limits transparency.
RISC-V, on the other hand, relies on an open, community-driven framework. Its compliance process uses openly shared test suites, golden reference models, and extensible frameworks like RISCOF. This open approach encourages innovation and flexibility but requires strong governance to prevent fragmentation across multiple independent designs.
The following sections detail each methodology’s operation and highlight its strengths and trade-offs.
ARM Compliance Methodology
ARM manages compliance through a proprietary process that guarantees consistency across all licensed implementations. At its core, the Architectural Validation Suite (AVS) is supplied in binary form to licensees to ensure instruction-set adherence. ARM also provides Fast Models as golden simulation environments to support verification.
Compliance is enforced at multiple lifecycle stages: design, pre-silicon, and post-silicon validation. The approval mechanism rests solely with ARM, the final authority for compliance. This approach is underpinned by a culture of continuous verification, with extensive test cycles applied throughout the IP lifecycle. The model provides strong reliability and consistency, but at the cost of limited transparency for the broader ecosystem.
Proposed RISC-V Compliance Methodology
By contrast, RISC-V International governs compliance through an open and structured framework. The process starts with a test-writing methodology, where minimal assembly programmes target each instruction or feature. These are executed using the RISCOF framework, which compares outputs from the design under test with golden reference models such as Spike, SAIL, or OVPsim.
ISA subsets group the curated Architectural Test Suite, while coverage is extended with random test generators and analysis tools. Passing this suite is mandatory for any processor marketed as “RISC-V compliant,” with certification programmes now being formalised to provide stronger commercial assurance. This approach is transparent and extensible, though it depends on effective governance to prevent fragmentation as implementations proliferate.
Comparison at a Glance
Table 2 summarises the two approaches, highlighting differences in key governance, methodology, and transparency.
| Aspect | ARM Methodology | RISC-V Methodology |
| Governance | Proprietary, ARM is the ultimate authority | Open, managed by RISC-V International |
| Test Suites | AVS (binary only) | Architectural Test Suite (open, curated) |
| Golden Models | Fast Models (proprietary) | Spike, SAIL, OVPsim (open) |
| Certification | Implicit via licence, explicit in SystemReady | Formal certification under development |
| Flexibility | Constrained by ARM ISA rules | Many optional extensions require governance |
| Transparency | Closed, under NDA | Open tools, community contributions |
Table 2: ARM vs RISC-V Compliance Methodology
Broader Market Implications
The choice of compliance and certification strategy has far-reaching consequences.
- For software developers, robust compliance prevents fragmentation, ensuring applications run consistently across devices.
- Certification provides visible assurance for device manufacturers, reducing the risk of integration failures and warranty issues.
- For SoC vendors, rigorous compliance and verification frameworks reduce cost, accelerate schedules, and build customer confidence.
ARM’s tightly controlled methodology delivers stability for licensees, while RISC-V’s proposed collaborative approach encourages innovation but requires strong governance to prevent divergence. Industry standards such as PCIe and USB show that compliance plus certification strengthens trust and market adoption.
Conclusion
Verification, compliance and certification are three interlocking pillars that underpin modern semiconductor and software ecosystems. Verification ensures designs are correct, compliance confirms adherence to specifications, and certification provides independent assurance to customers.
RISC-V is building a compliance and certification framework that echoes successful models like USB and PCIe. The result will be greater ecosystem interoperability and more substantial market confidence.
As open ISAs mature, engineers and decision-makers will need clarity on these processes. Robust compliance frameworks are not bureaucratic hurdles but enablers of trust, time-to-market, and sustainable innovation.
Understanding the distinctions between verification, compliance, and certification is increasingly essential for organisations designing or evaluating processor IP. The evolution of RISC-V’s open compliance frameworks and emerging certification programmes will be central to ensuring ecosystem interoperability and sustained industry growth.
Learn more about the latest RISC-V compliance and certification initiatives directly from RISC-V International.

Written by : Mike Bartley
Mike started in software testing in 1988 after completing a PhD in Math, moving to semiconductor Design Verification (DV) in 1994, verifying designs (on Silicon and FPGA) going into commercial and safety-related sectors such as mobile phones, automotive, comms, cloud/data servers, and Artificial Intelligence. Mike built and managed state-of-the-art DV teams inside several companies, specialising in CPU verification.
Mike founded and grew a DV services company to 450+ engineers globally, successfully delivering services and solutions to over 50+ clients.
Mike started Alpinum in April 2025 to deliver a range of start-of-the art industry solutions:
Alpinum AI provides tools and automations using Artificial Intelligence to help companies reduce development costs (by up to 90%!) Alpinum Services provides RTL to GDS VLSI services from nearshore and offshore centres in Vietnam, India, Egypt, Eastern Europe, Mexico and Costa Rica. Alpinum Consulting also provides strategic board level consultancy services, helping companies to grow. Alpinum training department provides self-paced, fully online training in System Verilog, UVM Introduction and Advanced, Formal Verification, DV methodologies for SV, UVM, VHDL and OSVVM and CPU/RISC-V. Alpinum Events organises a number of free-to-attend industry events
You can contact Mike (mike@alpinumconsulting.com or +44 7796 307958) or book a meeting with Mike using Calendly (https://calendly.com/mike-alpinumconsulting).
Stay Informed and Stay Ahead
Latest Articles, Guides and News
Explore related insights from Alpinum that dive deeper into design verification challenges, practical solutions, and expert perspectives from across the global engineering landscape.